Blues University is an ongoing series of articles geared towards beginner- and intermediate-level developers who are looking to expand their knowledge of embedded development and the IoT.
The Internet of Things (IoT) is a vast network of Internet-connected physical devices, from everyday household gadgets to sophisticated industrial equipment, constantly collecting and sharing data. The IoT's connected nature has far-reaching implications, offering unprecedented automation, optimization, and innovation opportunities across many sectors.
However, behind the seamless functioning of these devices is plenty of unnoticed magic. Just as the veins in our body transport blood to vital organs, network transport protocols in the IoT ecosystem ensure that data flows smoothly and efficiently between devices, servers, and applications. These protocols are essential in ensuring data exchange reliability, security, and speed, which are critical for IoT solutions.
Let's delve into these foundational frameworks, shedding light on common IoT transport protocol advantages, limitations, and ideal applications.
The Role of Transport Protocols in IoT
Transport protocols establish the guidelines and standards for device communication within a network. Think of them as traffic regulations for data, instructing each packet of information where, when, and how to move.
Transport protocols ensure that data is reliably transmitted and received. They also have to address the diverse requirements of IoT devices, such as limiting energy consumption, minimizing latency, or ensuring data integrity in unstable conditions.
How transport protocols operate determines several aspects of an IoT system:
- Reliability: Ensuring that the transmitted data reaches its destination without loss or corruption.
- Latency: The time it takes for data to travel from the source to the destination.
- Overhead: The additional data or extra load to manage and facilitate communication.
- Security: The measures in place to safeguard the transmitted data from unauthorized access or tampering.
- Energy efficiency: The protocol's energy consumption impacts the device's operational longevity, which is crucial for battery-operated IoT devices.
Transport protocols determine how efficient, secure, and reliable an IoT system is by dictating how data is packaged, transmitted, verified, and unpacked.
Next, let's explore the various transport protocols available for IoT systems.
Hypertext Transfer Protocol (HTTP)
The backbone of data communication on the Internet, HTTP facilitates the transfer of hypertext documents between web browsers and servers. Web pioneer Tim Berners-Lee designed it in 1990, and it's still how we access and view the Internet today.
Pros of HTTP
- Ubiquity: Being the de facto standard for web communication, almost every device with internet capabilities supports HTTP.
- Established infrastructure: Thanks to its long-standing history, there's a massive infrastructure already in place for HTTP, from servers and proxies to well-documented libraries.
- Compatibility: Because it's so widely used, HTTP easily integrates with various platforms, languages, and systems, providing a universal communication protocol.
Cons of HTTP
- Larger overhead: HTTP headers can be verbose, increasing data transfer sizes, which can be especially problematic for bandwidth-limited IoT devices.
- Statelessness: HTTP is stateless, so every request from a client to a server is considered a separate and distinct occurrence. This approach can be inefficient for IoT devices that require continuous monitoring or interaction.
- Suboptimal for low-power devices: The standard HTTP can be power-intensive, especially for devices that run on batteries and need to maximize energy efficiency.
HTTP Use Cases in the IoT
- Smart home devices: Many smart home devices, like thermostats, lights, and cameras, employ HTTP for remote control and monitoring through web interfaces.
- Web APIs for IoT: Many cloud platforms offer HTTP-based APIs, letting IoT devices send, fetch, or manage data through familiar web conventions.
Message Queuing Telemetry Transport (MQTT)
MQTT is a lightweight messaging protocol specifically for low-bandwidth, high-latency, or unreliable networks. IBM developed MQTT in the late 1990s to monitor oil pipelines over satellite connections. It's a client-server (or publisher-subscriber) based protocol, where the client interacts with a central server (a broker) to send or receive messages.
Pros of MQTT
- Lightweight: MQTT messages can be significantly smaller than those in protocols like HTTP, making it suitable for IoT devices with limited processing capabilities.
- Publish/subscribe model: Devices can subscribe to specific topics on the MQTT broker. It notifies all subscribers when another device publishes a message on that topic. This approach ensures real-time communication without constant polling.
- QoS levels: MQTT offers various quality of service (QoS) levels, enabling users to define how to confirm messages, ensuring reliability tailored to the specific use case.
Cons of MQTT
- Broker-based architecture: While centralizing simplifies many aspects of communication, it introduces a single point of failure. If the broker goes down, the communication chain breaks.
MQTT Use Cases in the IoT
- Home automation: MQTT has gained significant traction in home automation systems, enabling various devices to communicate state changes in real time.
- Remote sensors: Where sensors need to relay data from remote or challenging environments, MQTT's lightweight nature ensures efficient data transmission.
- Monitoring: Real-time monitoring systems, from industrial equipment to weather stations, use MQTT to send timely updates to central databases or dashboards.
Transmission Control Protocol/Internet Protocol (TCP/IP)
TCP/IP is the Internet's foundational pillar. This combination of the Transmission Control Protocol (TCP) and the Internet Protocol (IP) defines how data should travel across networks. While IP addresses and routes data packets to ensure they reach the correct destination, TCP ensures that the data packets are reliably delivered without errors.
Pros of TCP/IP
- Reliable data transfer: Because it's a connection-oriented protocol, TCP ensures that data sent from one end is reliably received at the other. Features like error checking and acknowledgment mechanisms are baked into TCP to guarantee data integrity.
- Widespread adoption: As the backbone of the Internet, TCP/IP is universally supported, making integration and compatibility relatively straightforward across devices and platforms.
Cons of TCP/IP
- Potential overhead: TCP's reliability comes with a cost. Its handshaking, error-checking, and acknowledgment mechanisms can introduce latency and overhead.
- Not always suitable for constrained devices: TCP's overhead is not ideal for IoT devices with limited processing power or battery life. It could reduce operational durations between charges or even overtax the device's capabilities.
TCP/IP Use Cases in the IoT
- Almost all Internet-connected devices: At some layer, nearly every device communicating over the Internet uses TCP/IP. While not every IoT device communicates directly using TCP/IP (some use more lightweight protocols for device-to-device communication), when they connect to broader networks or the Internet at large, TCP/IP usually comes into play.
User Datagram Protocol (UDP)
UDP is a transport layer protocol within the IP suite. Unlike its counterpart, TCP, which establishes connections and ensures data delivery, UDP operates on a "connectionless" paradigm. It sends datagrams or packets without establishing a connection, ensuring the receiver is ready, or guaranteeing that packets arrive in order (or even arrive at all!).
Because of its simplicity, devices often use UDP when speed and efficiency are paramount and some data loss is acceptable.
 note
noteCoAP operates over UDP.
Pros of UDP
- Fast: Without the overhead of establishing connections or ensuring packet order, UDP can transmit data quicker than many other protocols.
- Simple: The absence of complex handshaking and error-checking mechanisms simplifies its implementation.
- Low overhead: With no acknowledgment mechanism, this protocol uses fewer bytes, leading to minimal network overhead.
- Real-time communication: Its rapid nature enables real-time data transmissions, vital for time-sensitive applications.
Cons of UDP
- Unreliable: There's no data delivery, order, or integrity guarantee. Packets can be lost, duplicated, or out of sequence without mechanisms to handle these issues.
- No error recovery: If a packet gets lost during transmission, UDP doesn't have a mechanism to detect or recover it.
- No built-in security: UDP itself offers no security features, leaving data transmissions potentially vulnerable to eavesdropping or tampering.
UDP Use Cases in the IoT
- Sensor data transfer: In environments where sensors send frequent data, and occasional packet loss is tolerable, UDP offers a quick and efficient transmission method.
- Device discovery: When devices need to announce their presence or discover other devices on a local network quickly, UDP is a popular choice due to its broadcast and multicast capabilities.
Constrained Application Protocol (CoAP)
CoAP is a specialized web transfer protocol for constrained devices and networks, making it a prime choice for many IoT applications. Developed by the Internet Engineering Task Force's (IETF) Constrained RESTful Environments (CoRE) working group, many people consider CoAP a lightweight version of HTTP. It follows HTTP's RESTful principles, letting devices make requests and responses but with a design that caters to the unique needs of IoT devices.
Pros of CoAP
- Lightweight: CoAP has minimal overhead, which keeps packet sizes small and transmission times fast.
- Designed for constrained devices: CoAP acknowledges the limitations of IoT devices, ensuring that its requirements align with the capacities of devices with limited power, memory, or computational abilities.
- Support for DTLS: Datagram Transport Layer Security (DTLS) is incorporated within CoAP to offer a secure communication channel, similar to how HTTPS operates over HTTP but tailored for the constraints and demands of IoT.
Cons of CoAP
- Less widely adopted than HTTP or MQTT: Despite its IoT-specific design, CoAP isn't as widely adopted as protocols like HTTP or MQTT, which could limit community support and available integration tools.
CoAP Use Cases in the IoT
- Low-power sensors: Devices that run on minimal power, like battery-operated temperature or moisture sensors, benefit from CoAP's efficient power consumption.
- Devices with limited processing capability: Gadgets with little computational power or memory, such as simple actuators or beacons, can use CoAP effectively without protocol overhead bogging them down.
Matter
Formerly known as "Project Connected Home over IP" or "Project CHIP", Matter is an ambitious attempt to introduce a universal standard for smart home and IoT devices. Spearheaded by major tech giants like Apple, Google, Amazon, and the Connectivity Standards Alliance (formerly called the Zigbee Alliance), the project aims to foster greater compatibility and interoperability between smart devices, regardless of the manufacturer. By developing an open-source, royalty-free connectivity standard, Matter's advocates hope to simplify the smart home landscape for developers and consumers alike.
Pros of Matter
- Open-source: Matter's open-source nature encourages community contributions, promotes transparent development, and prevents vendor lock-in.
- Unifying standard for smart home devices: If it becomes the universal standard for smart home gadgets, Matter will resolve the fragmentation of the current smart home market, enabling devices from different manufacturers to work together seamlessly.
- Built with security in mind: Given the sensitive nature of home data and controls, its makers have architected Matter with a strong focus on security, ensuring encrypted communications and robust authentication.
Cons of Matter
- Still relatively new: Being in its early stages, Matter is still undergoing refinements and has not yet realized the full extent of its capabilities and stability.
- Yet to be fully adopted: While backed by significant industry players, Matter's success depends on widespread adoption by device manufacturers and developers. It remains to be seen how quickly and extensively they will embrace it.
Matter Use Cases in the IoT
- Smart home devices: From smart thermostats and lighting systems to security cameras and door locks, Matter aims to be the foundational protocol allowing devices to interconnect effortlessly.
- Consumer electronics: Beyond the traditional smart home gadgets, Matter has potential applications in broader consumer electronics, facilitating integration with televisions, speakers, and more.
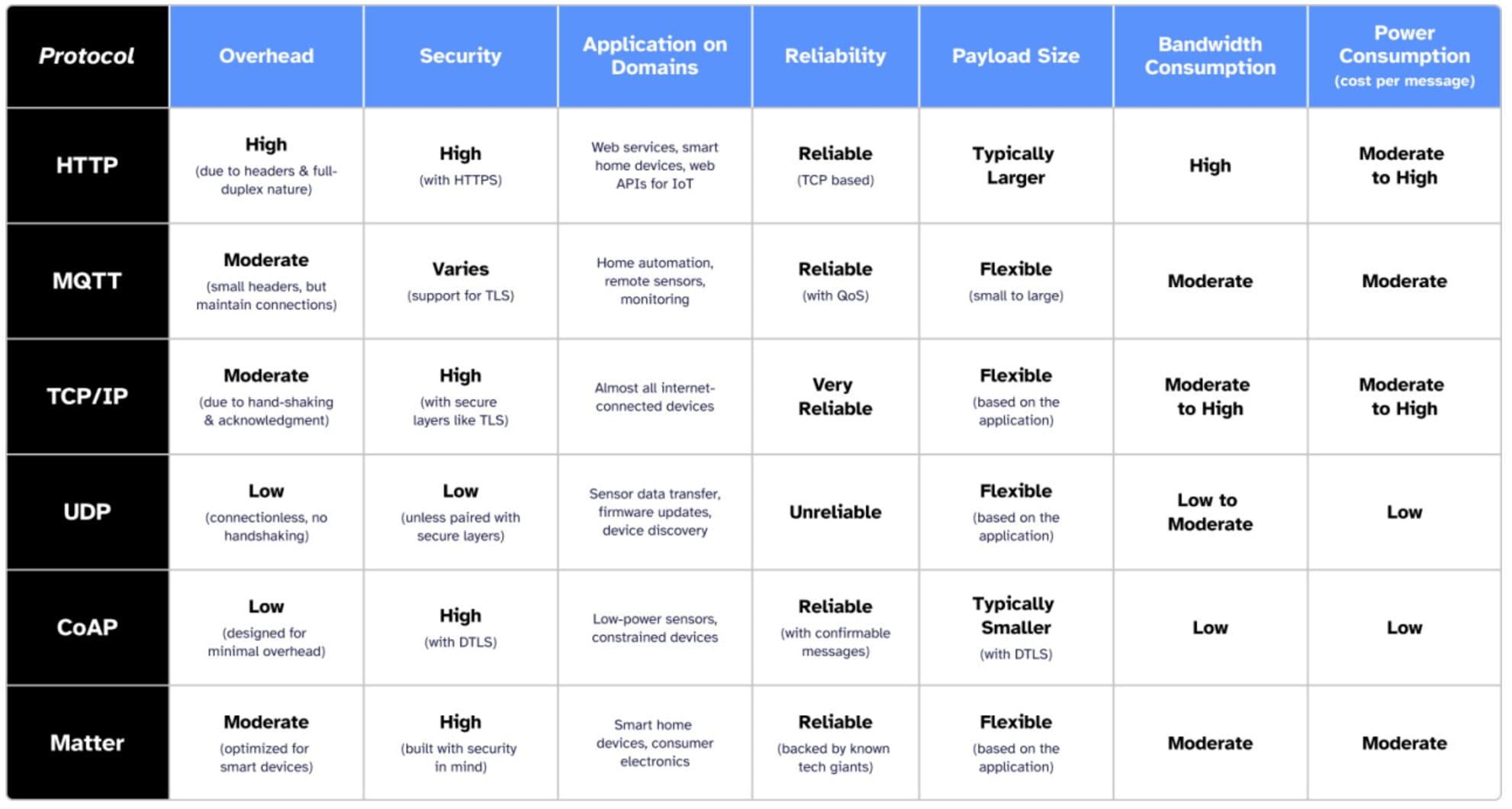
Comparing the Protocols
Selecting the ideal protocol for IoT use cases hinges on a blend of technical requirements, constraints, and desired outcomes. The table below sums up each protocol's strengths and weaknesses:
Security Implications
While the IoT increases device interconnectivity, it also increases security risk. Selecting a protocol that either inherently supports secure communication or can be supplemented with additional security measures is essential.
Let's examine each protocol's vulnerabilities and how it addresses security.
HTTP
- Security measures: The secure version of HTTP, HTTPS, employs SSL/TLS protocols to provide encrypted and secure communication.
- Vulnerabilities: Regular HTTP doesn't encrypt data, making it susceptible to eavesdropping attacks. Also, improperly configured or outdated HTTPS can have vulnerabilities.
MQTT
- Security measures: Supports Transport Layer Security (TLS) for encrypted connections. It also provides user authentication mechanisms.
- Vulnerabilities: If not using a secure connection, (MQTTS) transmits data in plain text. Retained messages might pose risks if not managed properly.
TCP/IP
- Security measures: As a foundational protocol, TCP/IP doesn't embed security features. However, layers built upon it, like TLS, can secure data transmission.
- Vulnerabilities: Susceptible to SYN flood, IP spoofing, and other attacks, especially if not paired with security protocols.
UDP
- Security measures: UDP itself is barebones and doesn't offer security mechanisms. However, combining it with protocols like DTLS can enhance security.
- Vulnerabilities: Being connectionless, UDP is susceptible to spoofing and denial-of-service (DoS) attacks. Attackers can also exploit its lack of built-in error recovery.
CoAP
- Security measures: Incorporates DTLS to offer secure communication channels, enabling encryption and authentication.
- Vulnerabilities: Data is exposed if not using the secure version of CoAP (CoAPS). As with any protocol, misconfigurations or outdated implementations can open vulnerabilities.
Matter
- Security measures: Developed with a strong emphasis on security, Matter ensures end-to-end encrypted communication and leverages industry-standard cryptographic primitives. Its open-source nature enables robust peer reviews, providing continuous security refinements.
- Vulnerabilities: Potential vulnerabilities could emerge since it's a relatively newer protocol.
No protocol is impenetrable, so an IoT system's security doesn't solely hinge on its transport protocol. Proper configuration, continuous monitoring, timely updates, and a holistic security approach that considers all layers, from the hardware to the application, are crucial.
Summary
Understanding these protocols is more than a beneficial skill. It's part of the essential knowledge foundation for every IoT developer and implementer.
This article serves as part of a broader series where you can dig deeper into components of embedded development and the IoT. To continue on this journey, be sure to follow Blues University.
If you're new to embedded development and the IoT, the best place to get started is with the Blues Starter Kit for Cell + WiFi and then join our community on Discourse. 💙